- Best Online Hash Cracker
- Sha1 Password Crack
- Online Hash Cracker Free
- Password Hash Cracker online, free
- Online Hash Cracker Pmkid
Ntlm is often used to encrypt Windows users passwords. It's the new 'version' of LM, which was the old encryption system used for Windows passwords. This website allows you to decrypt, if you're lucky, your ntlm hashes, and give you the corresponding plaintext. This is the new and improved version of md5 engine.If you put an md5 hash in it will search for it and if found will get the result. This is the beta 0.23 of this engine. You can see the queue of the hashes here. Bots will run thourgh the queue and use various techniques to crack the hashes. Security question, please solve.
Welcome to the Offensive Security Rainbow Cracker
Enter your Hash and click submit below. Support types: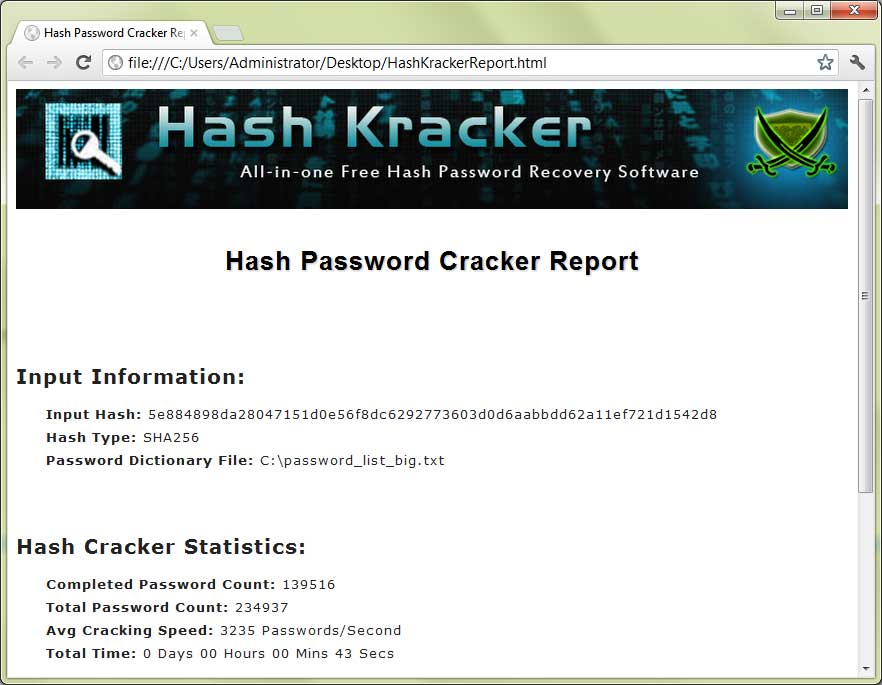
- - LAN Manager (LM)
- - Example: F1F7ADA0FE4A2881AAD3B435B51404EE
- - Hash length should be 32 bytes
- - Used as default on older Windows environments (Off by default on Windows Vista/Server 2008)
- - Case-insensitive
- - Maximum password length: 142
- - Both LM and NTLM hashes
- - PwDump format: LM:NTLM
- - ...or: User:ID:LM:NTLM:::
- - Example: F1F7ADA0FE4A2881AAD3B435B51404EE:FF94686ED6EC5222AB70C90D82A8E853
- - Hash length should be 65 bytes
- - Can be used to obtain the correct case for the password
Check out our current table hashset!
Best Online Hash Cracker
Due to abuse, the cracker has been closed to the public. We tried, we really did. Offsec students will find the priority code in their Control Panel.
Submit Your Hash
Currently Queued Hashes:
| ID | Type | Status | |
|---|---|---|---|
| 1377 | LM | WIP | |
| 1968 | LM:NTLM | WIP | |
| 2003 | LM:NTLM | WIP | |
| 2607 | LM:NTLM | WIP | |
| 3236 | LM:NTLM | WIP | |
| 3303 | LM:NTLM | WIP | |
| 3502 | LM:NTLM | WIP |

Last 40 Unique Hashes:
| ID | Type | Plaintext | Status | CrackTime | |
|---|---|---|---|---|---|
| 4849 | LM:NTLM | *NOT-FOUND* | Done | 0.00s | |
| 4848 | LM | *NOT-FOUND* | Done | 362.40s | |
| 4847 | LM | *NOT-FOUND* | Done | 440.19s | |
| 4846 | LM | *NOT-FOUND* | Done | 438.12s | |
| 4845 | LM:NTLM | *NOT-FOUND* | Done | 0.00s | |
| 4844 | LM:NTLM | *NOT-FOUND* | Done | 0.00s | |
| 4843 | LM:NTLM | starwars24 | Done | 45.20s | |
| 4842 | LM:NTLM | *NOT-FOUND* | Done | 293.44s | |
| 4841 | LM | *NOT-FOUND* | Done | 364.23s | |
| 4840 | LM | *NOT-FOUND* | Done | 365.62s | |
| 4839 | LM | *NOT-FOUND* | Done | 367.95s | |
| 4838 | LM | *NOT-FOUND* | Done | 367.18s | |
| 4837 | LM | *NOT-FOUND* | Done | 470.28s | |
| 4836 | LM | *NOT-FOUND* | Done | 458.96s | |
| 4835 | LM:NTLM | *NOT-FOUND* | Done | 0.00s | |
| 4834 | LM | *NOT-FOUND* | Done | 636.71s | |
| 4833 | LM | *NOT-FOUND* | Done | 651.43s | |
| 4832 | LM | *NOT-FOUND* | Done | 621.73s | |
| 4831 | LM:NTLM | *NOT-FOUND* | Done | 0.00s | |
| 4830 | LM:NTLM | *NOT-FOUND* | Done | 0.00s | |
| 4829 | LM:NTLM | *NOT-FOUND* | Done | 0.00s | |
| 4828 | LM | *NOT-FOUND* | Done | 367.07s | |
| 4827 | LM | *NOT-FOUND* | Done | 462.33s | |
| 4826 | LM | *NOT-FOUND* | Done | 451.05s | |
| 4825 | LM | *NOT-FOUND* | Done | 375.85s | |
| 4824 | LM | *NOT-FOUND* | Done | 368.67s | |
| 4823 | LM | *NOT-FOUND* | Done | 368.87s | |
| 4822 | LM | *NOT-FOUND* | Done | 362.92s | |
| 4821 | LM | *NOT-FOUND* | Done | 365.58s | |
| 4820 | LM:NTLM | *NOT-FOUND* | Done | 0.00s | |
| 4819 | LM | *NOT-FOUND* | Done | 645.27s | |
| 4818 | LM | *NOT-FOUND* | Done | 648.90s | |
| 4817 | LM | *NOT-FOUND* | Done | 624.27s | |
| 4816 | LM | *NOT-FOUND* | Done | 378.82s | |
| 4815 | LM:NTLM | *NOT-FOUND* | Done | 0.00s | |
| 4814 | LM | *NOT-FOUND* | Done | 374.82s | |
| 4813 | LM | *NOT-FOUND* | Done | 378.52s | |
| 4812 | LM | *NOT-FOUND* | Done | 482.87s | |
| 4811 | LM | *NOT-FOUND* | Done | 466.69s | |
| 4810 | LM:NTLM | egukeg41 | Done | 113.49s |
Last 40 Cracked Hashes:
| ID | Type | Plaintext | CrackTime | |
|---|---|---|---|---|
| 4843 | LM:NTLM | starwars24 | 45.20s | |
| 4810 | LM:NTLM | egukeg41 | 113.49s | |
| 4809 | LM:NTLM | wozofa66 | 68.39s | |
| 4808 | LM:NTLM | cacozi39 | 83.96s | |
| 4802 | LM | AKEN2390@34KDN | 208.47s | |
| 4756 | LM:NTLM | #=+C4#b | 40.80s | |
| 4755 | LM:NTLM | %ka9Z`U | 28.03s | |
| 4754 | LM:NTLM | qiKk8yz | 73.45s | |
| 4753 | LM:NTLM | i0$6B 9 | 62.59s | |
| 4752 | LM:NTLM | '=Cxu&L | 47.08s | |
| 4751 | LM:NTLM | racecar1234 | 94.78s | |
| 4750 | LM:NTLM | ectoplasm32 | 88.22s | |
| 4728 | LM:NTLM | Dbg30%1xan23 | 142.56s | |
| 4727 | LM:NTLM | Dbg29%1xan23 | 97.97s | |
| 4714 | LM:NTLM | 1985 | 54.76s | |
| 4713 | LM:NTLM | 1985 | 54.38s | |
| 4712 | LM:NTLM | 1985 | 54.69s | |
| 4711 | LM:NTLM | 1985 | 54.45s | |
| 4710 | LM:NTLM | 1985 | 55.11s | |
| 4707 | LM:NTLM | 1985 | 53.30s | |
| 4706 | LM:NTLM | DS^8DWLHFPI4QK | 2804644.32 | |
| 4702 | LM:NTLM | DA$6HktCjvet9Q | 53.84s | |
| 4687 | LM:NTLM | 1985 | 43.12s | |
| 4686 | LM:NTLM | OFFSEC | 104.69s | |
| 4658 | LM | PASSPASS | 115.13s | |
| 4657 | LM:NTLM | sj@5YmYa7J8L3I | 55.26s | |
| 4644 | LM:NTLM | HTG | 128.23s | |
| 4643 | LM:NTLM | HTG | 122.46s | |
| 4642 | LM:NTLM | HTG | 146.88s | |
| 4641 | LM:NTLM | HTG | 124.81s | |
| 4603 | LM:NTLM | Tigers123! | 85.52s | |
| 4577 | LM:NTLM | haveibeenowned | 67.04s | |
| 4576 | LM | HANS | 34.34s | |
| 4574 | LM:NTLM | AdMiN13680 | 46.19s | |
| 4554 | LM | CCSGDA_ | 21.31s | |
| 4546 | LM:NTLM | fE!2XbTpq2pjgq | 55.10s | |
| 4533 | LM:NTLM | Cad28dncwqn29 | 106.67s | |
| 4532 | LM:NTLM | DSnma8ine128 | 56.85s | |
| 4455 | LM:NTLM | bob123 | 103.39s | |
| 4452 | LM:NTLM | Y6#6BroIWottMX | 236.31s |
Tool to decrypt / encrypt with hash functions (MD5, SHA1, SHA256, bcrypt, etc.) automatically. The hashing of a given data creates a fingerprint that makes it possible to identify the initial data with a high probability (very useful in computer science and cryptography).
Answers to Questions
How to calculate/encode a hash?
The hash functions use computer data (in binary format) and apply nonlinear and non-reversible functions with a strong avalanche effect (the result is very different even if the input data is very similar). The fingerprint is usually returned as hexadecimal characters.
Example:dCode has for hashMD5e9837d47b610ee29399831f917791a44
Example:dCode has for hashSHA115fc6eed5ed024bfb86c4130f998dde437f528ee
Sha1 Password Crack
Example:dCode has for hashSHA256254cd63ece8595b5c503783d596803f1552e0733d02fe4080b217eadb17711dd
See the dCode pages for each hash function to know how it works in detail: MD5, SHA1, SHA256, etc.
How to decrypt a hash?
The principle of hashing is not to be reversible, there is no decryption algorithm, that's why it is used for storing passwords: it is stored encrypted and not unhashable.

Example:123+456=579, from 579 how to find 123 and 456? This is not possible except by trying all possible combinations.
The hash functions apply millions of non-reversible operations so that the input data can not be retrieved.
Hash functions are created to not be decrypable, their algorithms are public. The only way to decrypt a hash is to know the input data.
What are rainbow tables?
Theoretically, a brute-force mode is possible by testing all the binary strings, but a short message of 6 bytes already represents 281,000 billion combinations. Even with fast processors capable of performing millions of hash calculations per second, several days, months or years of calculations are therefore necessary to try all the possibilities in order to find a single hash.
However, users generally always use the same passwords and some characters more than others, so it is possible to store the most likely binary strings and their respective hashes in a very large dictionary. These dictionaries are called rainbow tables. These tables make it possible to test all the words of a given dictionary to check if their fingerprint corresponds to a given one.
Example: dCode uses its word and password databases with millions of pre-calculated hashes.
If the word is not in the dictionary, then there will be no result.
Online Hash Cracker Free
How to recognize a hash?
A hash can take many forms, but the most common are hexadecimal strings: 32 characters 0123456789abcdef for the MD5, 40 for the SHA-1, 64 for the SHA-256, etc.
The encoding system based on bcrypt uses the symbol $ followed by a number indicating the algorithm used and its possible parameters.
What is a salt (for a hash)?
The rainbow tables (gigantic databases of hash and password matches) are growing day by day and accumulating passwords stolen from various sites, and taking advantage of the computational performance of super calculators, allow today to decipher short passwords in minutes / hours.
In order to counter this technique, it is recommended to add salt (some characters in prefix or suffix) to the password/message. In this way, the precalculated tables must again be calculated to account for the salt that systematically modifies all the fingerprints, the salting step. Passwords are salted.
Example:MD5(dCode) = e9837d47b610ee29399831f917791a44 and MD5 (dCodeSUFFIX) = 523e9a80afc1d2766c3e3d8f132d4991
What is a cost (for a hash)?
Cost is the measure of the resources needed to calculate a hash. In order to complicate the task of creating the rainbow tables, it is possible to complicate some hashes so that the calculations take several milliseconds or seconds, which makes the duration necessary for the attacks too great to be applicable.
What is bcrypt?
bcrypt is a library of cryptographic functions that applies recursion rules to hash functions. Natively, the notions of salt and cost are applicable.
Source code
dCode retains ownership of the online 'Hash Function' tool source code. Except explicit open source licence (indicated CC / Creative Commons / free), any algorithm, applet or snippet (converter, solver, encryption / decryption, encoding / decoding, ciphering / deciphering, translator), or any function (convert, solve, decrypt / encrypt, decipher / cipher, decode / encode, translate) written in any informatic language (PHP, Java, C#, Python, Javascript, Matlab, etc.) no data, script or API access will be for free, same for Hash Function download for offline use on PC, tablet, iPhone or Android !
Need Help ?
Password Hash Cracker online, free
Please, check our community Discord for help requests!
Online Hash Cracker Pmkid
Questions / Comments
